mSpy is one of the top parental control and monitoring software on the market.

98

Last Updated 3 days ago
SMS monitoring has come a long way, and the good news is that mSpy also offers this feature. Let me share with you my actual experiences and opinions about this function.
The ability to monitor SMS on Android and iOS devices is nothing new, but it’s an important feature that can’t be taken for granted. The first time I came across SMS monitoring was with mSpy, and I found it fascinating that this tool allowed me to directly access text messages from monitored devices.
I decided to put together an elaborate guide on how to use this tool. This article comes with my personal insights and experiences that should help you understand and use this feature efficiently.
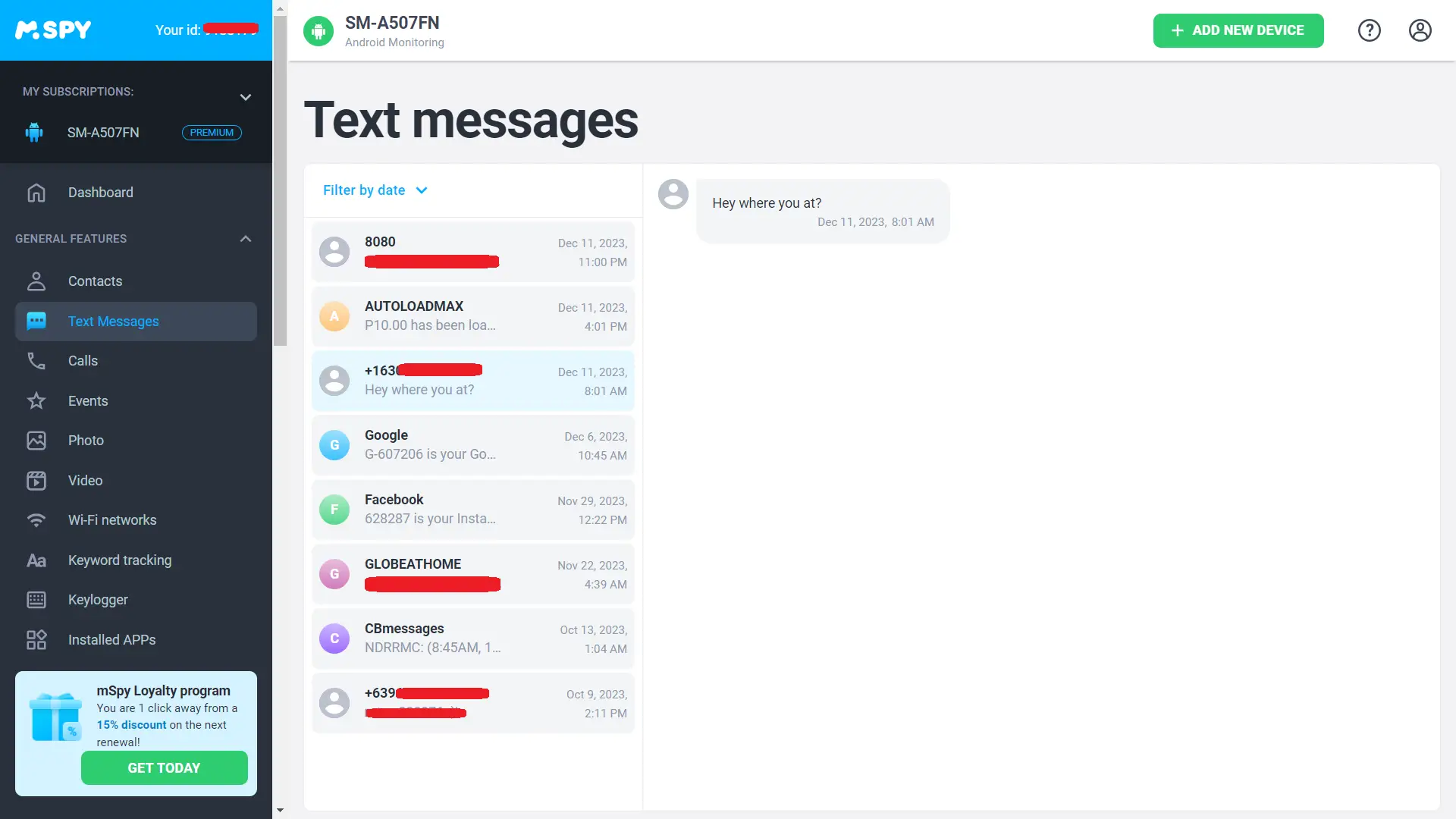
mSpy approaches SMS monitoring differently depending on the operating system used by the target device:
This method allows for comprehensive real-time monitoring because as soon as a message lands in their inbox, you can view it via the control panel.
This method seems less intrusive because it doesn’t require jailbreaking but also comes with some drawbacks:
It’s hard to give a straight answer whether you can recover deleted text messages using mSpy because much depends on the operating system used by the target device.
Here’s what I've learned:
If someone who is very tech-savvy gets their smartphone rooted, they could use dedicated tools or an adb shell command line utility to read someone else’s texts stored locally by their phone.
Apple protects user data with strong encryption mechanisms that thwart most recovery attempts including mSpy. If someone enabled end-to-end encryption for iMessage service or encrypted their entire phone storage with an impossible-to-crack passphrase (or worse – biometric authentication), the app won’t be able to help you recover these specific text messages.
I’ve been writing about spy apps for years now and let me tell you one thing: each time I sit down to write about another surveillance tool I feel like I need to remind my readers about ethics.
Monitoring other people is wrong unless we do that within legal boundaries defined by our local legislations and only when we have good reasons to do so.
SMS monitoring seems particularly dangerous when discussing ethical issues because these little snippets of text often carry sensitive information between friends or family members.
We’re talking about:
All these are examples from real life where spying upon someone’s texts might reveal more than we bargained for when using spy apps.
At the same time, there are legitimate uses for such tools like:
Conclusion
As a self-proclaimed tech nerd who likes analyzing technology dimensions through practical experiments, my deep dive into the SMS surveillance capabilities offered by mSpy resulted into several important insights:
Each platform requires individualized approach hence demands different strategies.
Android allows instant observation while iOS demands regularity plus patience waiting towards backup happening.
It might prove difficult regaining access onto deleted texts due various reasons mentioned above.
mSpy seems to be the perfect match for those who are looking for an efficient smartphone surveillance solution provided that they aren’t afraid of dealing with the technicalities of rooting plus handling the installation process.
 Related Articles
Related Articles
We've compiled a list of related articles
Learn how to effectively use mSpy for SMS tracking in our detailed guide. Keep tabs on messages for peace of mind and security.
Find out if mSpy can read deleted texts in our detailed guide. Gain valuable insights from firsthand experiences and expert advice on mSpy's features.
Our guide provides insights on overseeing your child's text messages, ensuring their digital communication is secure.
Master SMS monitoring on your husband's phone with our guide. Gain peace of mind and understanding in your digital communication journey.
Find out how to effectively monitor employee SMS communication while respecting privacy and legal boundaries in our detailed guide.
Learn how mSpy tracks SMS, multimedia messages, and social chats with stealth and accuracy, providing a full overview of text communications.
Get insights into mSpy's text tracking on multiple platforms. Our guide covers compatibility, installation, and ethical considerations.
Learn how mSpy monitors SMS communications with our comprehensive guide. Find out about its key features, privacy aspects, and practical uses.